The management of users.
Finally got the device talking to the Firewall.
They call this Dynamic access privilege management architecture.
Alright.
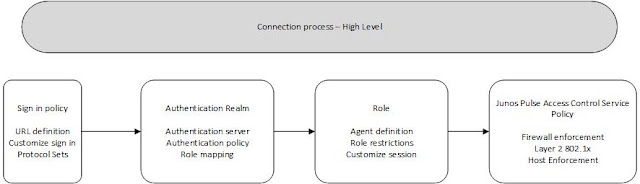
Sign in policy.
Define the URL
one for admins /admin
the other for the users.
The Sign-in policy defines which realms will be available for the users.
The above is the signing in page.
You can see the administrator URLs we have configured
and the User ones.
*/ means nothing besides the https://name_of_device
/admin remember is to get to the admin.
Then you create other ones for fun.
To each you can make a sign-in page, either customized or reg
then assign an Authentication domain that will authenticate the users.
The last checkbox is simply to enable it.
Then Authentication Realm.
AAA is the Authentication server, the credentials are forwarded to it.
Authentication policy- you set rules like checks before it sends your data to the server AAA
Directory Server is an LDAP that gives you user and group information that will be mapped to roles.
Role Mapping rules. You map them to the roles you want to create in the MAG.
User role - defines properties for users like session. A user can have many roles.
Role restriction - You can limit the role attachments by forcing it to pass more checks for the role.
Resource access policy- to protect a SPECIFIC resource.
- It can use the enforcement points
- It can add additional items like
- source interface it must come through
- Auth Table mapping
- IP address pool assignment to assign him an IP
Network access policies - Layer 2 policies that control the 802.1x settings on the enforcement points.
They define the Radius data that the MAG will send to the enforcement 802.1x points.
Connection Process - High Level.
User Authentication process.
I don't know,
Print this part above out and study it.
It's made from three parts.
- What the USER does
- What the MAG Secure Access device does
- What the AAA does - The AAA is made up from the
- Authentication Server
- (Ldap/AD) server will give you the groups
It's divided in the Authentication process. Once that part is done the MAG will look for the Authorization
which means what is the user actually allowed to do.
At the end it will send the relevant data to the enforcement points.
Authentication
First part is the host
Second part is credentials
Third part is sending the credentials to the AAA
then
Authorization
MAG queries the LDAP for groups
Maps groups and user to role
Applies role restrictions
Creates a session user role
then
Enforcement
Sends the data required to the endpoints
Policies and Auth table entries
The endpoints are.
Firewalls
802.1x switch , accesspoints
OAC
Case Study 1::
The device works in a non restrictive fashion.
So if the role allows it but another denies it , you will get the allow permission.
User Interface policy is applied the first policy.
maximum session length will be the "highest" value.
If you get two roles and one has a requirement you did not pass, then you can access only ONE role.
Host Enforcer can also check if the policy permits access to the RESOURCE.
not only if the HOST is ok.
Realm authentication
sign in policy
user role
role restrictions
resource policies
network policies.
I


No comments:
Post a Comment