Scenario 1.
We have a LAN
The guys in the LAN will want to reach the Servers
The Firewall will block them till they reach the MAG
The MAG will tell the firewall to allow them.
They will get access.
Sounds Simple.
Let's see what simple is like with the MAG.
Alright connect the console cable to the SM160 or SM 360 module itself. (not the management one)
in the case of the smaller devices it is mixed in with the MAG
so for example.
Voila, anyway console to console port.
9600
8data bits
1 stop bit
no flow.
This is standard for Juniper.
The console in the MAG appliance is so you can set up an IP. The devices are mainly WEB managed
and don't run the JUNOS one OS marketing . They still run the web portal instead.
BOOT UP
When you boot the MAG Modules SM160 - SM360
You get to select the personality.
Secure Access Service - this is for the SSL gateway
Access Control Service- this is so you can use it as a NAC internally on the network.
remember one option is for the SSL the second is as a NAC LAN device.
please choose from among the following factory-reset-personality images:
[1] Junos Pulse Secure Access service
[2] Junos Pulse ACCESS CONTROL service
so we choose 2.
It can take 20 minutes to install the device. Jeez, well take a break and get a sandwich.
Then you get the license agreement.
If you are bored or need to prolong the installation press R to read it.
If not press Y .
Interface configuration.
nothing new here.
IP
Subnet
Gateway
DNS
second DNS (optional)
DNS domain blogspot.com
WINS (optional)
Then it asks you to review and confirm.
Press Y enter
Ok, this configured port 1
Port 1 is in the middle
Port 0 is for OOB management and is configured from the WebUI
Ok,.
After that you create an admin user and his password.
This is mainly for Console and for first access.
Alright, this device uses Certificates. Yes, those annoying pop ups we dismiss because they are outdated
or badly kept. This is a security device so certificate.
The next stage in the CLI is generating one.
Common NAME - my-mag-AC.blogspot.com
organiztion blogspot.com
hit some random characters and press enter.
Then you get the certificate and the device telling you , you are DONE.
CLI menu.
The CLI menu is kinda 1980's .
You choose a numbered option.
- network Settings and tools - has ping ARP
- Admin password -did that
- display log - ok system logs
- system operation - ? reboot or reset to factory
- Toggle password protection for the console- turn on admin on console
- Create a Super admin session - ? locks out everybody else and let's you in
- System Snapshot - ?? saves settings to backup file
- reset allowed Encryption strength for SSL - you can drop it from 128 to 40-bit cipher like K8
from Cisco so you can export it to Iran.
Ok, from here it is all WEB.
What fun, memorizing screenshots.
What fun, memorizing screenshots.
username password and disregard the certificate that does not work yet
(You can make it work by getting a real certificate from the CA)
when you connect using the IP certificate warning always appears.
Sorry, hard to get any screenshots.
I guess you can buy a MAG. You'd need a 4610
You can also try Ingram Micro they have a lab.
The last choice is begging Juniper for access to their labs.
Anyway.
This is the way the screen looks.
You have the main Toolbar on the left.
SYSTEM - obvious + logs
AUTHENTICATION- servers
ADMINISTRATORS- set admin users
USERS - - realms and roles for them.
UAC - rules to connect to the firewall.
MAINTENANCE - archiving
This screen is for the Secure Access
not the Access Control.
You can quickly tell that by the lack of the UAC on the left side menus.
and when you hover over something it opens sub menus. rolling the mouse
or click on what you want .
Alright
Tab called Guidance at the corner.
Wizards.
When this is the first time it will pop up or you can invoke it or dismiss it.
Task 1.
Fake Task menu.
But you get the idea.
System Setup --> Set date and time
pick time zone
select either NTP server and give it an IP or set up the time manually.
Pulse -Firewall and CA must be on the same time if not SECURITY does not work.
Next upgrade the device.
Next install your licenses from License management system at http://juniper.com/generate_license.
You need the Hardware ID and authorization code you get when you buy licenses.
Base license comes with the device for 2 users.
Common Access License - you buy for the 'concurrent users'
Last is a Certificate.
System>> configuration > certificates > device Certificates new CSR
or you can use the wizard we are in.
A CSR is the data so a big Kahuna CA can make you a certificate which you can import.
Or you can use a self signed certificate.
CSR menu looks like this Certificate Signing request.
So you can save it as a .cert and email it to the CA
you can email it to the CA
you can paste the text into a CA portal.
Then you import back the response from the CA>
and voila you have a CA certified server.
then you have to tell the port to use the NEW certificate.
So you can set up different ports with different certificates ?? I guess.
Next you must import the cetificate of the Authorizing CA itself into the device.
This is the certificate of the CA of the certifying authority.
Screenshot place
Ok.
Now if we go to the UAC part of the menu
We can add a Firewall as an enforcer.
Must be Junos or Netscreen.
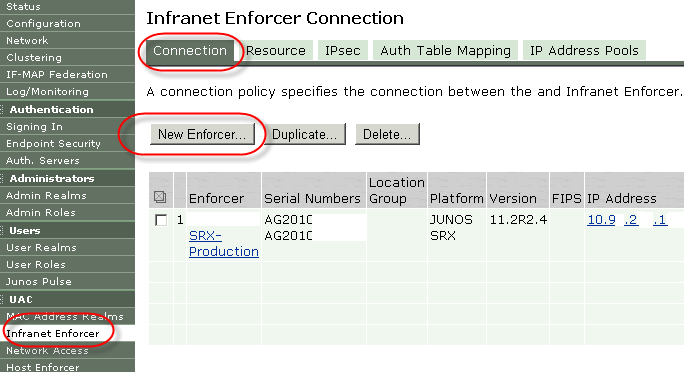
platform
Name
password
Serial - must be the Chassis hardware serial
{If you add a cluster you add two serial numbers}
Group
IDP module. {this is for enabling IDP scanning on the traffic}
IP
Configuring the ENFORCER - Firewall.
Set timezone date or NTP
root# set system time-zone America/New_York
run set date 201107130900.00
Set security zone MAG on the MAG interface
set security zones security-zone MAG address-book address AC1 172.168.13.1/32
set security zones security-zone MAG host-inbound-traffic system-services ping ssh ssl
set security zones security-zone MAG interface ge-0/0/2
### so you added an address for it and allowed ping/ssh/ssl as services that can hit the zone
### then you add an inteface to the zone
Set a hostname for the infranet-controller
set services unified-access-control infranet-controller AC1
set services unified-access-control infranet-controller AC1 address x.x.x.x
set services unified-access-control infranet-controller AC1 interface ge-0/0/2.2
set services unified-access-control infranet-controller AC1 password my_secret_pass
ok I guess this is still easy.
Set up IP
set up interface to MAG
set up a password and a name of the infranet-controller.
Set up the zone
add an interface to it
add the MAG address to the address book
root# show services
unified-access-control {
infranet-controller AC1 {
address 172.16.0.5;
interface fe-0/0/2.0;
password "$9$pZt90Ic8X-dwgO1Nb2gDj0BIclMLxdY2a"; ## SECRET-DATA
next you can
set services unified-access-control infranet-controller AC1 ca-profile AC
basically this will use the same CA certificate of the CA master, so it can verify the MAG
Certificate. This is optional.
commit and-quit
Verifying.
Check the STATUS window.
Green ok
White not good.
- UAC > INfranet Enforcer > Connection
Verify the IP and Serial of the enforcer
Verify the - System --> log events --> log for id=GWE*
then you can see the connection events for tips .
On the firewall enforcer.(SRX)
>show services unified-access-control status
should say connected the interface IP Host port etc.
TroubleShooting
From the MAG
- Maintenance >>Troubleshooting >> tools >> commands
you can do ping ARP traceroute etc. to help troubleshoot.
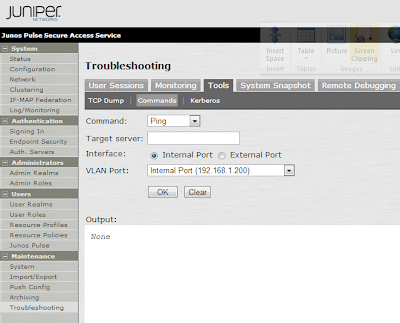
On the Firewall
Verify
time date timezone
routing
zone interface permissions PING SSH SSL must be allowed on host-inbound-interface
certificates if using.
must sync the clocks up to 5 min apart
must use the hardware serial ID and authorization code to generate the licenses to add to the device.








No comments:
Post a Comment