This is the network today for most IT people.
Pretty much the usual.
If you have a branch you set up a VPN using IPSEC.
If you have users they get a VPN client and connect to the Firewall and then they have access to the whole
network.
If you have contractors it's a problem.
The same with Partners.
Most companies will set up a website or similar for the partner and contractors. However then
that website will need to be public.
The Firewall is your BORDER guard and protects you against the bad people.
This design is old.
For example. If your user takes his laptop home, connects to work. Then downloads some virus.
When he brings back the laptop to work. Your network will be infected.
The same if he brings in a USB with an infected file.
another old way to protect your network was to set up the Servers in a datacenter and call it a DMZ
and then add another firewall.
DMZ is great but the rest of your network is still full of viruses, keyloggers and people removing sensitive
information.
So how do you solve this.
- You need network protection based on the device.
- So for example an IPAD gets internet only.
- A contractor can access only the required server and none of the others
- A device can be evaluated to see if it safe to join the LAN
- You can place non qualified devices or users in a remediated VLAN so
they can correct the faults. - Diverse user access
- So admin can access all
- Accounting only accounting
- Guest can only access specific things
- Application-level control.
- By that they mean that you can only access the application but not the fileshare
- This is mainly driven by regulatory compliance requirements
- Visibility into who is doing what.
The solution is NAC. which we talk about here.
it must be simple, proven and integrate easily.
If it's not simple, it sucks.
If it is some random company then you will be begging for support
You should not have to redesign the network to get it to work.
If it's not simple, it sucks.
If it is some random company then you will be begging for support
You should not have to redesign the network to get it to work.
NAC network access control has no perimeter.
Every device is assumed to be un-safe until you allow it.
Because it evaluates every device, the role and permissions it can protect all of the network.
Every device is assumed to be un-safe until you allow it.
Because it evaluates every device, the role and permissions it can protect all of the network.
So we identify the device, then the user, then assign him a role(group) then the applications he can access, then we log it ALL.
We can also add additional controls like AV and signal bandwidth limits to other devices to enforce.
What Juniper's NAC solution looks like.
Ok.
So traffic goes through the firewall on the SSL or VPN ports
It is accelerated if needed by the application acceleration.
Then the communication is handled and terminated by the SECURE ACCESS .
Secure access determines if you can CONNECT.
then the Access control can determine if they are allowed to USE the program
So traffic goes through the firewall on the SSL or VPN ports
It is accelerated if needed by the application acceleration.
Then the communication is handled and terminated by the SECURE ACCESS .
Secure access determines if you can CONNECT.
then the Access control can determine if they are allowed to USE the program
then you reach the data.
So far so good.
3 appliances each with a role.
3 appliances each with a role.
They also added mobile Security
With Mobile security you can control the security on the SmartPhones. For example deleting data, applications or finding lost phones.
So
Accelerator
Secure Access to terminate the connections
Access control to control devices
Mobile Security to control the security of smartphones.
Depending on what you use you can customize the Junos pulse to load only those
parts on the end client.
The usual user list can be Radius, RSA, LDAP, Active Directory etc.
The devices can affect the behavior of other devices. For example if Access control does not like PC2
it can tell the Switch to block the port (assuming this is an intelligent switch 802.1x)
The firewall can allow IPs or set up VPNs
it can tell the Switch to block the port (assuming this is an intelligent switch 802.1x)
The firewall can allow IPs or set up VPNs
So the client
Junos pulse is the agent or supplicant
Junos pulse is the agent or supplicant
The switch is 802.1x along with the firewall and hostchecker are the enforcers - authenticator
and the Gateway- SA AC is the Authenticating server
and the Gateway- SA AC is the Authenticating server
and the Radius is the authenticating server. - The SA can also transfer the requests to it.
Gateway does
AAA by connecting to those servers authentication , authorization , accounting - users, roles
Radius for 802.1x the MAG can work as a Radius or connect to an external Radius.
Endpoint assessment and fixing. This is done using HostChecker uses IMC integrity measurement collector
NAC can send remediation instructions by reviewing the IMV measurement verifiers to correct the host.
NAC can send remediation instructions by reviewing the IMV measurement verifiers to correct the host.
The AGENT is
Junos Pulse
Junos Pulse
Odyssey client
Java
Java
Agentless HostChecker
third party TNC supported.
third party TNC supported.
Enforcement points are.
802.1x switches and AP
SSG or SRX firewall. they are called Firewall enforcers.
Host Enforcer is part of the OAC does client side enforcing of policies
Host Enforcer is part of the OAC does client side enforcing of policies
Junos Pulse Gateway
E voila
the appliance.
It is a centralized management device- you web into it and control the settings.
It can authenticate users to roles and resources.
You get a user he gets a role and a policy is applied
this policy is pushed dynamically to the endpoints.
{{it can use some standards like LDAP to get groups, AD for groups, PKI for certificates, Siteminder/
NIS for user SSO, }}
{{802.1x supports some sub protocols like EAP-TTLS m EAP-JUAC(juniper) , EAP-TLS,EAP-GTC (Token uses a one time code) , EAP-SoH statement of health}}
Delivers software like Junos Pulse, Odyssey,Java, OAC applications to the endpoints and talks to them.
So it can check for compliance using host Checker for policy in 802.1x you can place them in other VLAN
till they fix themselves.
host Checker uses IMC and IMV integrity measurement collectors while the
gateway uses the IMV integrity measurement versifier. TNC is the structure.
It is purpose built and hardened.
You get a user he gets a role and a policy is applied
this policy is pushed dynamically to the endpoints.
{{it can use some standards like LDAP to get groups, AD for groups, PKI for certificates, Siteminder/
NIS for user SSO, }}
{{802.1x supports some sub protocols like EAP-TTLS m EAP-JUAC(juniper) , EAP-TLS,EAP-GTC (Token uses a one time code) , EAP-SoH statement of health}}
Delivers software like Junos Pulse, Odyssey,Java, OAC applications to the endpoints and talks to them.
So it can check for compliance using host Checker for policy in 802.1x you can place them in other VLAN
till they fix themselves.
host Checker uses IMC and IMV integrity measurement collectors while the
gateway uses the IMV integrity measurement versifier. TNC is the structure.
It is purpose built and hardened.
SA vpn will go to AAA uses data groups host checker and can give remediation.
Junos Pulse.
Alright,
802.1x obviously.
IPSEC support for setting up a tunnel after authentication.
Source IP for allowing the IP access after authentication
Integrated Host Checker.
IPSEC support for setting up a tunnel after authentication.
Source IP for allowing the IP access after authentication
Integrated Host Checker.
location and identity aware
Smart card
logs on client side also troubleshooting tools.
You can either deploy it from the MAG if the laptops have administrator rights.
You can also install it using active directory.
You can either deploy it from the MAG if the laptops have administrator rights.
You can also install it using active directory.
Windows
Odyssey access client
this baby is used for windows/mac/linux
802.1x
IPSEC
Source IP
Integrated host checker
Cool - client side firewall
When you disconnect it stops running the access policies on your laptop.
IPSEC
Source IP
Integrated host checker
Cool - client side firewall
When you disconnect it stops running the access policies on your laptop.
Java Agent
MAC and Linux
Runs in the background
no 802.1x support :(
No IPSEC support :(
Runs a heart beat so when you disconnect it stops the policies.
Runs in the background
no 802.1x support :(
No IPSEC support :(
Runs a heart beat so when you disconnect it stops the policies.
HostChecker.
Agentless, runs on Linux, MAC, Windows.
dynamically downloads hostchecker
no 802.1x
no IPSEC
Must keep an open browser for it to live.
Agentless, runs on Linux, MAC, Windows.
dynamically downloads hostchecker
no 802.1x
no IPSEC
Must keep an open browser for it to live.
Third Party
must support 802.1x standard
TNC
or both.
Microsoft NAP for example.
IP phone with 802.1x support is another.
Phones without 802.1x support must rely on the MAC authentication server.
must support 802.1x standard
TNC
or both.
Microsoft NAP for example.
IP phone with 802.1x support is another.
Phones without 802.1x support must rely on the MAC authentication server.
Enforcement points. - Security devices
Layer 3 to 7 uses the Firewall Junos or ScreenOS
They get instructions from the Access Control Services it dynamically updates them.
Source IP available for everybody agent or agentless it does not encrypt
IPSEC, you can signal the Firewall to run an IPSEC tunnel from the firewall to the device.(Pulse,OAC)
The MAG provisions the Firewall Enforcement points with Dynamic policies.
HTTP redirect. if the switch gets a request that does not have an authentication in place
it can redirect it to the Access Control MAG. This only works for HTTP.
it can redirect it to the Access Control MAG. This only works for HTTP.
So Source IP based enforcement.
Alright.
So 1. Authenticates to the Secure Access MAG.
2. the MAG tells the SRX to allow that IP in.
2. the MAG tells the SRX to allow that IP in.
3. The SRX writes a permit rule.
4. The Laptop can access the server. (this is un-encrypted)
So much fun.
4. The Laptop can access the server. (this is un-encrypted)
So much fun.
Same thing but with IPSEC.
Alight same thing.
1. authenticate
1. authenticate
2. set up the VPN
3. VPN in
4. Access the server.
Must have JUNOS PULSE or OAC client to do this.
Enforcement points 802.1x we said are switches and Accesspoints.
Check the datasheets to see if they support this protocol.
Port based enforcement for switches
Association for APs , they will drop the association of the client if he fails.
Check the datasheets to see if they support this protocol.
Port based enforcement for switches
Association for APs , they will drop the association of the client if he fails.
802.1x is the codename here.
They can Dynamically assign the client a VLAN based on the results of his check
They can also filter applications or change QoS attributes.
You can use 802.1x or combine it with the Firewall enforcement.
They can Dynamically assign the client a VLAN based on the results of his check
They can also filter applications or change QoS attributes.
You can use 802.1x or combine it with the Firewall enforcement.
So
Junos pulse works only on windows.
Junos pulse works only on windows.
OAC agent Windows / MAC
All the rest work on everything else.
IPSEC works only on Windows
Source IP works on everything
802.1x because it blocks ports works on everything.
Host Enforcer of rules only OAC on Windows. (this can block something on the end client)
Host Enforcer of rules only OAC on Windows. (this can block something on the end client)
Ok, those are the components.
Now let's see how the components INTERACT
Now let's see how the components INTERACT
So the supplicant uses 802.1x
talks to the switch.
The switch checks the Pulse gateway to see
talks to the switch.
The switch checks the Pulse gateway to see
The Pulse also checks the supplicant to see if he is OK as far as security
then asks the AAA if he is allowed to do anything.
and then sends the 802.1x the allow him on and gives him access.
then asks the AAA if he is allowed to do anything.
and then sends the 802.1x the allow him on and gives him access.
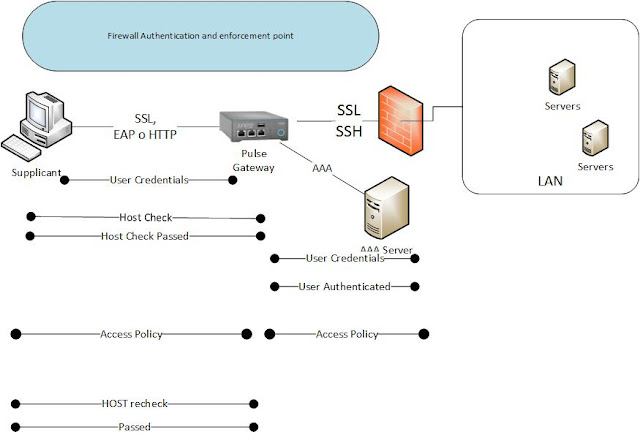
If the connection is external.
Same thing as before.
The device goes to the MAG using SSL or EAP-over-http.
The MAG checks the AAA
The MAG tells the firewall to open up.
The Firewall sets up a connection or an opening
Client can access the servers.
The device goes to the MAG using SSL or EAP-over-http.
The MAG checks the AAA
The MAG tells the firewall to open up.
The Firewall sets up a connection or an opening
Client can access the servers.
In case of failure I can put him in a temp vlan and tell him to remedy something.
Host Check
Then you pass the credentials to AAA
then you can come in and reach the LAN servers.
Same thing but with the Firewall.
Then you pass the credentials to AAA
then you can come in and reach the LAN servers.
Same thing but with the Firewall.
Deployment.
- Front End is the MAG before the Firewall.- This is the easiest to deploy and is for when you don't use 802.1x
- WAN gateway - this in the opposite as you control the traffic going out, for example what guests can send and that the devices meet the hostchecker security.
- Campus Wired - Devices must access the Gateway to enter the network
the same for phones and MAC devices. So you control the LAN. - Campus Wireless- same thing but with Wireless since you already have a user password experience this is a good place for initial deployment of the NAC.
- MAC address authentication - Allows you to control which MAC addresses are allowed on the LAN
Questions
What are the components.
- Junos Pulse access control - Gateway
- Endpoint software - agent, agentless
- Enforcement points - 802.1x or firewall
Enforcement options.
802.1x - Switch or Access point
Firewall - Junos or SSG IPSEC or IP based
Endpoint - OAC or Junos can run IPSEC and Host-enforcer(OAC).
802.1x - Switch or Access point
Firewall - Junos or SSG IPSEC or IP based
Endpoint - OAC or Junos can run IPSEC and Host-enforcer(OAC).
Secure Access Model.
You connect using Layer 2 to the MAG it will push your settings to you.
You connect to MAG remotely then it will push settings to the Firewall for you to enter.
Endpoint options are.
Pulse
OAC - remember an odyssey on the sea.
Java
Agentless










No comments:
Post a Comment