Question: 1
A customer wants to create a custom Junos Pulse configuration. Which two are required?
A. Connection set
B. Configuration set
C. Custom installer
D. Component set
Answer: A, D
Ok,
Junos Pulse is the software.

Remember it can do many things like acceleration and other things.
In this case we want to create a Custom configuration which will only have SOME of the items.
Instead of ALL of the items.
Lab3-3
- USERS > Junos Pulse > Connections > new Connection set
The connection determines the client settings.
Then in the next tab components
we select "new component set"
Then we select the "minimal components (only components needed to support the selected config are installed )
Answer C is a custom installer.
In OAC you can use a "preconfigured file" which does sound like a custom installer.
However the question was about Pulse.
Answer B
Configuration set. no such thing.
Question: 2
What type of firewall enforcers are supported by the Junos Pulse Access Control Service?
Answer SSG and SRX
The SRX was configured using the CLI
the SSG we did it using the Management GUI.
Question: 3
A customer is trying to decide which 802.1X inner protocol to use on their network. The customer
requires that no passwords be sent across the network in plain text, that the protocol be supported
by the Windows native supplicant, and that the protocol supports password changes at Layer 2.
Which protocol would meet the customer's needs?
A. EAP -TTLS
B. EAP -MD5
C. PAP
D. EAP -MSCHAPv2
Answer: D
This is more of an elimination challenge.
PAP is clear text so scratch it.
Windows is made by Microsoft , MS is short for Microsoft so MSchap would be supported by microsoft.
That is the answer.
Question: 4
You have a Junos Pulse Secure Access acting as an IF-MAP client, configured to federate all
user roles to a Junos Pulse Access Control Service acting as an IF -MAP Federation server.
A remote user using Junos Pulse logs in What happens next?
A. The Junos Pulse Secure Access Service redirects the user to the Junos Pulse Secure Access Service
for authentication
B. The Junos Pulse Access Control Service provisions enforcement points to enable resource access
for that user.
C. The Junos Pulse Secure Access Service publishes user session and role information to the IF-MAP
Federation server,
D. The Junos Pulse Secure Access Service provisions enforcement points to enable resource access
for that user.
Answer: C
The Answer is C easily simply because logically an IF-MAP client will update the IF-MAP server.
Question 5:
What is the first action you need to do after consoling in to the MAG appliance.
A. Set up a password
B. Set up an admin user
C. Import license
D. Select a personality.
The answer is D, you select either the SA or AC Access Control Service
What is the function of Host Enforcer?
A. To force clientless access to the network
B. To enforce restrictions on access to protected resources on the network
C. To scan an endpoints for compliance with security policies
D. To push a firewall policy to the endpoint's local firewall application
The answer is D. Host items run on the endpoint.
Host Checker will check the settings
Host Enforcer will configure the endpoint with your selection of rules.
Scott Newman, Courseware Developer
More questions from Juniper.
You are the administrator of a cluster.
You notice that the passive node takes a long time to respond and take over.
How do you improve the speed of change.
A. Change the inactivity timeout
B. Change the heartbeat
C. Change the Auth table timeout.
D. Change the number of ARP ping failures
Answer is D.
In the Cluster properties.
- System >> Clustering >> (click on the cluster) >> properties
there is a network healthcheck settings. In it you change the
"number of ARP ping failures before interface is disabled [3]
Auth table has nothing to do with this.
Heartbeat, the only heartbeat we have is from the AC to the AJAX Java agent and the
heartbeat of the Role Session parameters.
Inactivity timeout is from the Sessions

None of this is for Clustering Active/Passive except for D.
Question
Which of the two configuration settings will be the same on the two members of the Junos Pulse Access
Control Service Cluster.
A. Virtual Ports
B. User Roles
C. Authentication Server information
D. Routing tables.
Answer B and C
User Roles are synchronized.
Both devices must use the SAME authentication server.
So the settings will be identical.
Routing tables could be different depending on the location of the device.
Virtual Ports - there are no "virtual ports" on the MAG.
Question.
Where do you define the OAC configuration when creating a preconfigured install for the OAC.
OAC user interface
Odyssey settings
OAC administrator
OAC component set.
OK. Component set is from Junos.
The Odyssey settings are local to the endpoint
the OAC user interface is local to the endpoint.
So OAC administrator.
I quote "" to create an installer, you can use the OAC administrator to set the OAC configuration that you want, then export the settings into a zip file.
Options include hiding or disabling configuration icons, allowing users to modify adapter settings, or preventing them from disabling the OAC.
The installer also includes license keys.
So use the OAC administrator , create a customized OAC in a zip file.
Then use that as your preconfiguration file :
Question.
A user is running Linux which options can he use (two)
A. Java agent
B. Agentless
C. Odyssey access client
D. Junos Pulse.
Pulse - works for windows.
OAC - windows and MAC
Agentless - on everything.
Java agent - on anything that can run Java , since Linux can run Java.
The answers would be A and B.
Question.
You want to enable Guests some access. Which client would you offer them if you cannot install anything
on their laptops.
A. agentless
B. Host Checker
C. Anonymous
D. Junos Pulse.
Anonymous does jnot exist.
Host checker checks for compliance to the IMV only .
Pulse is a full client you must install
So Agentless A would be the correct choice.
Question.
You want to limit the number of features a ROLE will have in their Junos Pulse client.
What do you use to limit the number of features.
A. Junos Pulse connection type
B. Location awareness
C. Junos pulse client components.
D. Junos preconfiguration installer.
preconfigured or preconfiguration should ding OAC in your head.
connection type controls the connection
location aware will determine if the user is in the WAN , LAN or other.
Junos pulse has Client Components.
Role >> Junos pulse client components > New Component Set >>
junos pulse client components.
here you select the nice.
All components
No components
Minimal components which is just for the features you selected.
Question
Which three sign-in policy components are valid ?? Choose 3.
A. User Role Mapping
B. Host Enforcement
C. Authentication Protocol Set
D. Sign-in URL
E. Authentication Realm.
This is what a "NEW sign-in policy " window looks like.
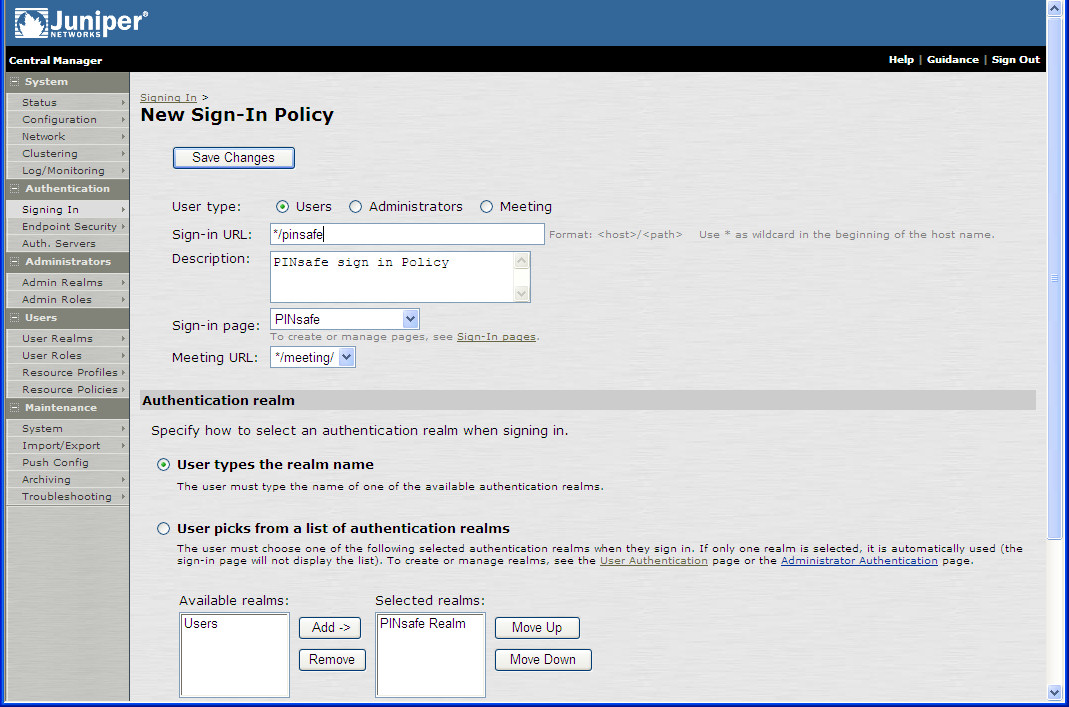
In it you create a SIGN-IN where users SIGN-IN.
So Sign-in URL should be easy to get.
Every sign-in page leads to some sort of Authentication Realm .(LDAP,Radius,none)

The last one is the Authentication Protocol Set.
(the top screenshot is for an SA and not an AC, sorry screenshots are scarce)
The Authentication protocol set is the option to add 802.1x to the sign-in
So all those 3 will give you the sign-in policy requirements.
Host Enforcement is on the
Host Checker Policy - which is under
>> Authentication >> Endpoint Security
User Role Mapping is done at the User Authentication Realms >>
Question.
OK, this one looks smart.
You administer the network , which has a NEW real using the Junos Pulse Access COntrol Service.
A User complains to you that they can access the network
but they cannot access the Accounting Server.
What are three explanations for this.
A. The user is being subjected to the Host Enforcer Policy
B. The User is subject to a role restriction.
C. The User is failing the host checker policy at the realm level.
D. The user is not mapped to the proper role.
E. The user is entering the incorrect authentication parameters.
So here you use the triage. The ITIL word for eliminating what cannot be possible.
E. The user is entering the incorrect password. - This cannot be because then he would not have ANY
access and we are told he can reach the rest of the network.
C. The user is failing the host checker policy at the REALM Level. - This cannot be because if he was
failing at the REALM level he would not be allowed in.
So the answers are the rest of the A,B,D
Questions
What are the Three Secure Access Control Service Enforcers.
A. Radius Enforcing Server
B. Host Enforcer
C. Infranet Enforcer
D. 802.1x Switch.
802.1X can enforce 802.1x authentication protocol Set.
Infranet Enforcer means the SSGor SRX Firewalls that can enforce IP source or IPSEC or other.
Host Enforcer can run on the client endpoint and enforce some rules of choice.
Radius is not an Enforcer it is an AUTHENTICATING SERVER
Question
You are creating ROLE mapping rules using your "local database" option.
Which two methods would you choose.
A. Group Membership
B. User Attributes
C. Certificates
D. Usernames
The catch here is the Local""
If it LDAP or remote then you would use Groups or Attributes.
HOwever since it is local.
Just use
USERNAME.
The CErtificates is a bit harder as I simply remembered there was an option for that in the lcoal database.
Yeah,
In the Local Database your choices when running the "role mapping rule"
are
Username.
Certificate
Custom Expressions.
Question
Which two parameters do you define for a user role.
A. Type of Agent Access methods
B. Custom user interface
C. Prohibited application.
D. Resource Policy.
So if you remember defining a user.
We selected what methods can he use like Pulse/ OAC/ Agentless
The last TAB was UI options where you can change the background and replace the Juniper image
with your company logo.
We don't have a "prohibited application" in the MAG.
Resource Policy is defined on the INFRANET ENFORCER
Comment
MAC Authentication Server.
MAC authentication Realm.
Both are unique to the MAC thing as you can tell by the big MAC in front.
The best EAP methods are.
EAP-TTLS
EAP-JUAC
EAP-MD5
EAP-GEneric Token Card.
So token card is with tokens
EAP-MD5 is very old from server 2000
Juac is the Juniper one and is the default.
TTLS is the best too.
Question.
On the MAG series device a Sensor event is configured with the action "replace user role" and make it permanent.
The MAG has quarantined a user based on a sensor event from an IDP.
In the MAG device GUI how do you release him from the Quarantine.
I'll save myself typing all the poisibilities.
It will NOT be in System>>Status >>Users simply because that would be the system users and not the
end users.
It will be in AUTHENTICATION > AUTH SERVERS >> srv >> tab users select the user
and click ENABLED to release the USER from Quarantine.
Question or reference to CAs
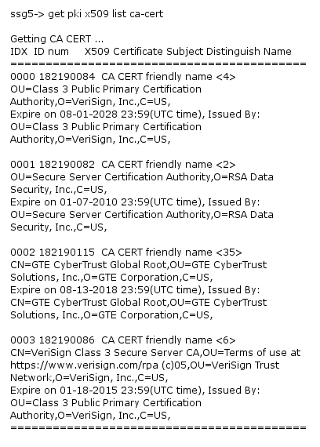
You might get some CA questions.
Remember.
o= organization.
In this example o=Verisign
C= country
ou= organizational unit. in LDAP this could be a group.
you should also look at Expiry times.
Expire on 01-07-2010 is no good.
FTP = SCP the only difference is the S for Secure Secure Copy Protocol.
There might be a few of these. MAG supports both.
Question
Set Security unified-access-control
Set access unified-access-control
Set services unified-access-control
set security UAC
Which is the correct one.
Very difficult to tell.
From the configs I remembered it was unified-access-control
Access I know is where you define access profiles for users and groups.
Security is where you define the zones and policies.
In the policy we had THEN permit application-services UAC-Policy
so I guess services.
EAP-TLS uses PKI
No comments:
Post a Comment