Requirements:
- Authenticator must support Dynamic configuration using the Radius attributes it will be getting back
- Authenticator must communicate with the Junos pulse Access control (Radius)
- 802.1x enabled on the device and the ports.
- Attributes like the VLAN must be configured on the device
- If assigning Vlans dynamically - a DHCP must be available for the VLANs
Example
Any employee goes on employee VLAN
contractor go on contractor VLAN
Failure or guest go on remediation VLAN.
Each device on route to the supplicant must be configured as an 802.1x layer 2 enforcer.
Adding the RADIUS server to the SRX.
system {
time-zone America/New_York;
}
radius-server {
172.16.0.101 {
secret "$9$zFusF9p0ORSlM1Rs4ZjPf1RhcyK"; ## SECRET-DATA
timeout 4;
retry 2;
source-address 1.1.1.12;
access {
profile AC1 {
authentication-order radius;
radius {
authentication-server 172.16.0.101;
OK. So the first one sets up the Radius server.
The second one creates an access profile. Sets up the order of authentication to use RADIUS
then adds the server to use. Which is the one we created first.
The second one creates an access profile. Sets up the order of authentication to use RADIUS
then adds the server to use. Which is the one we created first.
1.1.1.12 is the SRX
172.16.0.101 is the MAG Radius
On the 802.1X switch
protocols { # the stanza we will use
dot1x { # 802.1x
authenticator { # mark the switch as an authenticator
authentication-profile-name AC1; #profile access
interface {
ge-0/0/2.0 { # interface , usually you can mark all in the switch
supplicant single; #single supplicant can apply at a time.
guest-vlan REMEDIATIONVLAN; #guest vlan for non authenticated
server-reject-vlan REMEDIATION; # Vlan for rejected clients.
That way the REMEDIATION vlan can only have access to the Web
So they can correct their flaws like update the AV or the patches.
So they can correct their flaws like update the AV or the patches.
Configuring the 802.1x on the MAG
All of this will be applied on the initial connection as they connect.
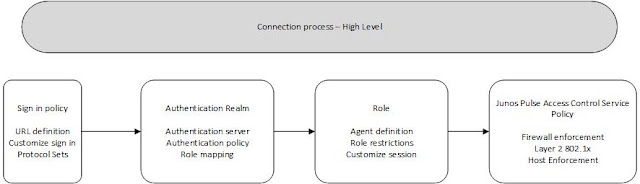
The PROTOCOL Set is in the sign-in policy .
That is where we will configure it.
That is where we will configure it.
Steps.
Verify There is a Dictionary. - Remember the dictionary of attributes.
Each dictionary is a manufacturer one.
Each dictionary is a manufacturer one.
UAC > Network Access > Radius dictionary.
extreme.dct
juniper.dct
You can verify the RADIUS vendor list
This is only if you are not using the default list.
Add the Authentication Protocol Set
First select the Authentication Protocol , the order matters and it will try the EAP-TTLS first.
The specify the INNER authentication protocol to use.
In this case it will be under the TTLS block.
It will try EAP-JUAC the Juniper one first.
Then PAP
then CHAP
In this case it will be under the TTLS block.
It will try EAP-JUAC the Juniper one first.
Then PAP
then CHAP
Then it will try the EAP-PEAP here you specify the innter authentication too. It will show under the PEAP box.
In this case it is again EAP-JUAC.
In this case it is again EAP-JUAC.
the order matters.
Once you selected the Authentication protocol set
You will create or use the current Sign-in policy.
In the sign-in policy you will select the Authentication protocol you just created.
You select the Authentication protocol in the REALM. ---> Authentication protocol.
You will create or use the current Sign-in policy.
In the sign-in policy you will select the Authentication protocol you just created.
You select the Authentication protocol in the REALM. ---> Authentication protocol.
So I guess you apply it to the REALM.
Location Group
You can create a location group for people depending on where they sign in.
You can apply this sign-in policy to tha location group.
???
You need to configure EACH 802.1x authenticator as a RADIUS client.
uAC >> netowrk access > RADIUS client select the make and model and add a location group.
Next you can configure the RADIUS Attribute.
This is the ATTRIBUTE that will be sent from the RADIUS to the Authenticator once
you ahve made it.
This is the ATTRIBUTE that will be sent from the RADIUS to the Authenticator once
you ahve made it.
UAC >> Network ACcess > Radius Attributes
you create a policy and select the LOCATION group. Then you add the RADIUS attributes you want to add.
Then you can make it more granular by selecting which ROLES will this apply to.
Second Example.
You can add an attribute that the Device must be with so and so IP.
Pulse
Outer EAP-TTLS
inner EAP-JUAC
MAC authentication Server
authentication > AUTH server new MAC address authentication
add the MAC addresses.
add the MAC addresses.
or set up an LDAP server for the MAC addresses to be received from.
then
Create a new REALM
UAC > MAC address Realm. new
UAC > MAC address Realm. new
point to the MAC AUTH server you created.
then when the device comes in the user can select that realm
or you can apply that Realm to devices.
or you can apply that Realm to devices.
Location Group associates devices with a policy.
MAC Auth Server MAC auth Realm are only for MAC addresses.
No comments:
Post a Comment